In traditional industrial systems, cyber security has relied on isolating networks (air-gapping) and limited connectivity. Digital transformation and Industry 4.0 have made interconnectivity essential, especially with technologies like AI and big data analytics, which offer benefits like predictive maintenance and optimized control. Yet, this shift increases vulnerabilities, leading to risks like operational disruptions and safety breaches. Many legacy systems need more cybersecurity, and upgrading them is costly, creating potential risks. As global regulations tighten, industries must adopt comprehensive security strategies, including audits and workforce training, to fully leverage digital advances while mitigating cyber threats.
To address these concerns, I wrote my Master’s thesis, “Managing Production Network Security with OPC UA.” The research involved an extensive literature review and the creation of a requirements engineering specification document for the development process of an OPC UA Security Manager application, which incorporates an OPC UA Global Discovery Server and Secure Keys Service.
The complete thesis is available in Aalto University’s Aaltodoc archive.
Automation Systems
OPC Unified Architecture (OPC UA) is a standardized communication technology that facilitates communication between various systems and devices. Achieving this with earlier technologies has been difficult, forcing factories and automation systems to generally have automation components from a single automation manufacturer.
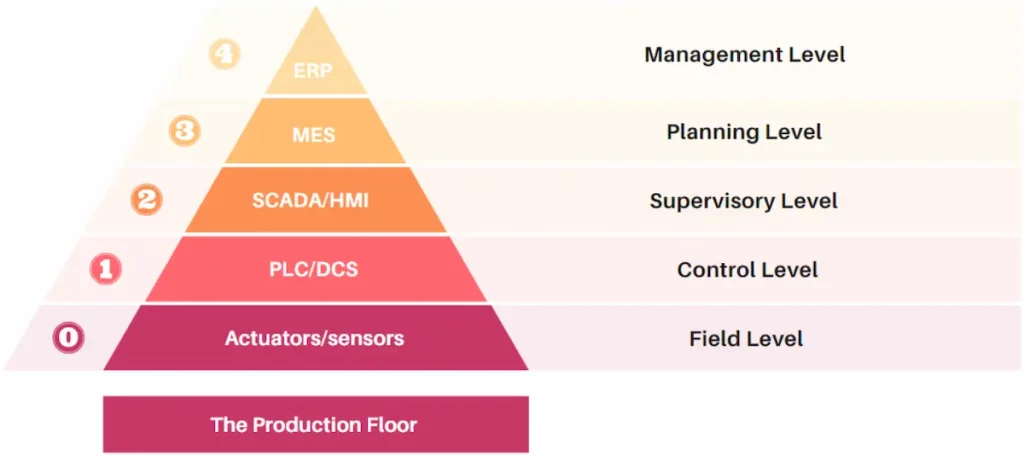
Figure 1 depicts a typical automation system with five levels, starting from the top with enterprise-level systems to the bottom level with sensors and actuators from ANSI/ISA-95 standard. Automation systems vary in size; even small embedded devices can be automation systems. However, this section focuses on factory-level automation systems, including systems and devices, to the top of the pyramid at Level 4.
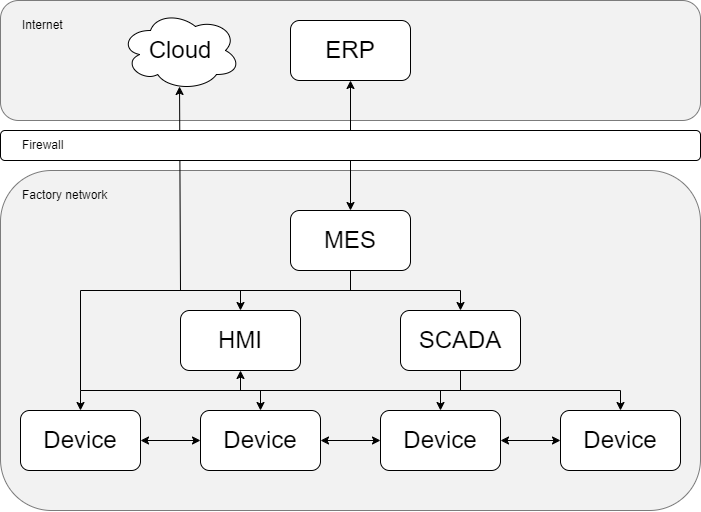
Figure 2 describes how automation systems are typically connected. Devices in the figure are a combination of Levels 1 and 0. This example system mainly uses Client-Server architecture. PubSub can connect to any part of the system, including the most miniature sensors and actuators. Still, it would be most beneficial for data gathering in MES, ERP, and SCADA. For example, connections to the Cloud in the figure are PubSub connections.
Security Compliance
Regulatory entities have been implementing various cybersecurity guidelines for the industrial domain to ensure the safety and security of critical infrastructure. Some examples include the NIST Cybersecurity Framework 2.0 (CSF), the ISA/IEC 62443 standards, and the EU’s Network and Information Systems (NIS2) Directive. These guidelines focus on risk management, threat detection and response, access control, and other measures to protect against cyber attacks on an organizational level. The motivation to follow these quite restrictive guidelines comes from the fact that NIS2 is not simply a recommendation or regulation; it is a legally binding framework enforced across the EU. Each member country is expected to integrate NIS2 into its legislation by October 17, 2024.
OPC UA Security
OPC UA functions across various components within an industrial facility, from top-tier enterprise-level management to low-level sensors and actuators. When utilized for enterprise oversight, OPC UA may interact with external entities like customers and suppliers. The OPC UA security architecture is a robust solution that enables the implementation of essential security features at various levels within the OPC UA Application architecture.
OPC UA Security Manager
The goal of the thesis was to form a software requirements engineering document that describes the functionality of an OPC UA Security Manager application (UASM). UASM is an all-encompassing security solution for OPC UA Client-Server and PubSub communication. Its goal is to improve the overall security of all OPC UA devices in networks that run under the management of a UASM. The goal is to make the setup process as simple as possible for users while offering a solution that can be installed and configured only once and then forgotten. Ease of use while improving security over currently existing solutions is the primary design philosophy
of the application. The core component of the UASM application is the Certificate Authority (CA), which generates and authenticates all certificates used by the Global Discovery Server (GDS) and Security Key Service (SKS).
Global Discovery Server
The Global Discovery Server (GDS) is an OPC UA Server that acts as an access
point for extended Certificate Authority in the OPC UA environment. GDS allows Clients to search for Servers within the administrative domain of the GDS. A GDS aims to simplify the creation, maintenance, and operation of large networks of OPC UA applications, improving scalability and security management across an industrial automation environment. Its services include discovering OPC UA servers and clients, managing security credentials, and facilitating the establishment of secure connections between OPC UA applications. However, the GDS’s most important ability is to create and manage application instance certificates and trust lists, which are critical for secure communication in OPC UA networks.
Security Key Service
Security Key Service manages message security in PubSub communication. The Publisher uses it to sign and encrypt NetworkMessages, and the subscriber uses it to decrypt the messages received from the Publisher. At the core of its functionality, the SKS manages SecurityGroups, which are the central elements in bridging the roles of different entities and the SecurityGroups they are part of.
Segmentation
Data and Certificates of an automation system are the most important elements to be safeguarded in an industrial network, so it is vitally important to ensure their safety. The ISA/IEC 62443 defines Zones and Conduits. Zones consist of a group of cyber assets that share the same cybersecurity requirements, and Conduits are the connections between Zones.
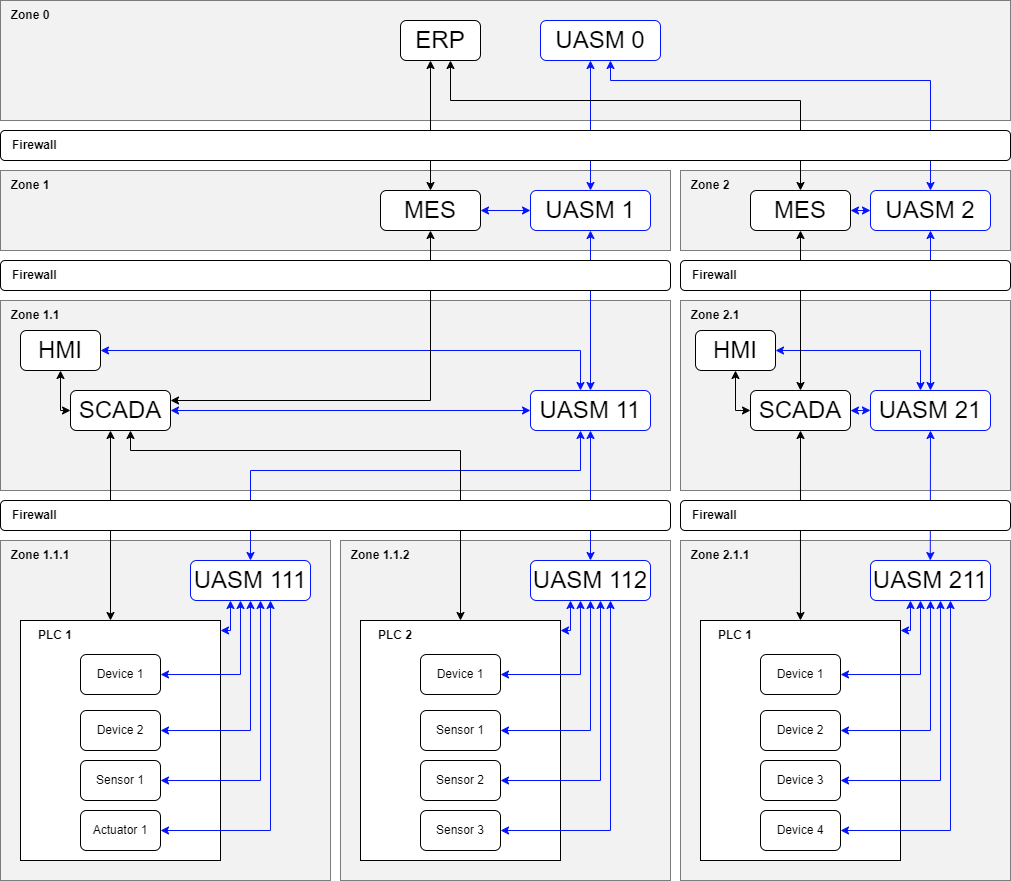
An example of this horizontally and vertically segmented system can be seen in Figure 3. It is possible to communicate directly from device to device. Corresponding ports need to be opened in the firewall, and a Certificate with access to both devices is required from a higher-level UASM. For example, we can see in Figure 3 that if PLC 1 from Zone 1.1.1 wants to connect to PLC 1 from Zone 2.1.1, it would need a Certificate from UASM 0 from Zone 0. Device-to-device communication between different plants is not usual, and ERP should be able to relay this kind of communication if needed. Normally, there would not be a reason to open Conduit to another industrial plant.
Ideally, all Zones would have their own UASM that only connects to the devices within the Zone and the UASM on the level directly above. There should also be a firewall between all Zones and all levels of the automation pyramid.
Conclusions
The following conclusions come directly from the thesis, and it is recommended that you read the complete thesis to understand them.
The thesis has explored OPC UA’s current cybersecurity capabilities in a factory automation environment. The objective of this research was to form a Software Requirements Specification (SRS) document for the OPC UA Security Manager (UASM) application, which incorporates a Global Discovery Server (GDS) and Security Key Service (SKS). OPC UA specifications and related research were investigated to evaluate the feasibility of such an application.
The industry needs to enhance cybersecurity, as threats are increasing, and regulatory authorities are enforcing legislation to ensure industrial bodies have strong cybersecurity. OPC UA specifications provide enough security features to counter current cybersecurity threats effectively. The issue is the lack of implementations that offer necessary features to the end users. Upgrading cybersecurity is hard and expensive, and as there are no off-the-shelf products to do this, it might even be impossible in some cases.
The study has shown that UASM when combined with current OPC UA security capabilities, enhances the security infrastructure of production networks by centralizing certificate management. This centralized approach not only reduces risks associated with manual security configurations but also improves the interoperability and efficiency of security operations across various automation systems. This is beneficial, especially in factory automation settings where the system might have tens of thousands of different automation devices with thousands of certificates.
To conclude, this research contributes to increasing the cybersecurity level of OPC UA networks widely used in automation systems. It lays the groundwork for the future development of solutions that can be implemented to counter evolving cybersecurity threats the industry faces.
Elias Nykänen
Software Engineer
